
Get 24/7 incident response assistance from our global team
- APAC: +65 3159 4398
- EU & NA: +31 20 890 55 59
- MEA: +971 4 540 6400
Get 24/7 incident response assistance from our global team
Please review the following rules before submitting your application:
1. Our main objective is to foster a community of like-minded individuals dedicated to combatting cybercrime and who have never engaged in Blackhat activities.
2. All applications must include research or a research draft. You can find content criteria in the blog. Please provide a link to your research or research draft using the form below.
Safeguard sensitive information with advanced data leakage prevention capabilities from Group-IB
Implement proven secure data practices along with a comprehensive data breach prevention strategy to avoid the significant negative consequences of data leaks
Leaked data involves compromised personal information, credentials, and other sensitive data that can be sold on underground forums or used for secondary attacks
exposed databases were identified by Group-IB in 2021
Regularly assessing a business’s security posture is crucial to defend against data leaks caused by critical vulnerabilities. The first step is to uncover hidden breaches with Compromise Assessment. During the procedure, Group-IB experts may use the Managed XDR solution for threat detection and response
Businesses often have a complex and extensive IT infrastructure, making it challenging to keep track of all its components. Shadow IT assets such as forgotten web applications or remote computers can carry a high risk of data leakage.
An Attack Surface Management solution helps continuously discover unmanaged IT assets and identify vulnerabilities in your ecosystem. Meanwhile, the expert Security Assessment provides a comprehensive analysis of the company’s infrastructure, allowing to discover hidden vulnerabilities, weak spots, and security risks.
The Endpoint Detection and Response module of the Group-IB Managed XDR solution protects computers and servers against data leaks by detecting breaches and attacks on the host level. It uses intelligence data, signature and behavioral analysis, and malware detonation capabilities. Group-IB Fraud Protection solution completes the endpoint protection by protecting web and mobile API endpoints.

Group-IB offers a full range of solutions for data leak detection. Group-IB Digital Risk Protection monitors open and dark web sources to detect sensitive data belonging to your organization that has leaked into the public domain. Group-IB Threat Intelligence helps discover compromised credentials, breached databases, and Git leaks. Thanks to continuous monitoring of the corporate infrastructure, Attack Surface Management allows you to spot potential sources of data leaks, while Managed XDR detects and prevents data exfiltration. The Compromise Assessment service enables you to detect the unnoticed breaches.
Like any cybersecurity incident, data leakage requires a prompt and professional response. The Group-IB Incident Response Retainer is a pre-negotiated statement of work that enables an immediate action to be initiated, blocking the data leak to reduce the scope of damage and avoid penalties.

Data leaks may result in the revocation of licenses or certifications and partial or even complete termination of a company's profitability
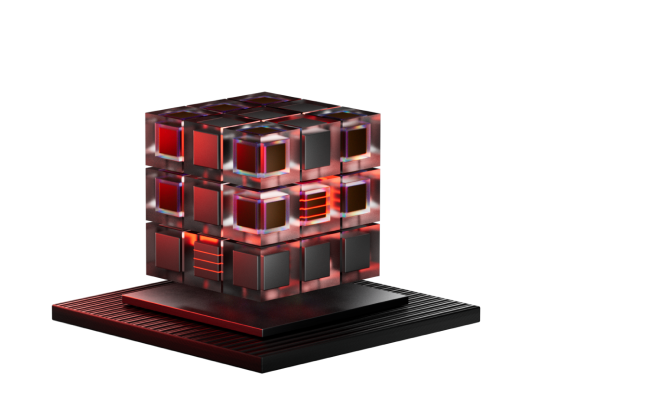
Average cost of a data breach globally in 2023
Regularly assessing a business’s security posture is crucial to defend against data leaks caused by critical vulnerabilities. The first step is to uncover hidden breaches with Compromise Assessment. During the procedure, Group-IB experts may use the Managed XDR solution for threat detection and response

Businesses often have a complex and extensive IT infrastructure, making it challenging to keep track of all its components. Shadow IT assets such as forgotten web applications or remote computers can carry a high risk of data leakage.
An Attack Surface Management solution helps continuously discover unmanaged IT assets and identify vulnerabilities in your ecosystem. Meanwhile, the expert Security Assessment provides a comprehensive analysis of the company’s infrastructure, allowing to discover hidden vulnerabilities, weak spots, and security risks.

The Endpoint Detection and Response module of the Group-IB Managed XDR solution protects computers and servers against data leaks by detecting breaches and attacks on the host level. It uses intelligence data, signature and behavioral analysis, and malware detonation capabilities. Group-IB Fraud Protection solution completes the endpoint protection by protecting web and mobile API endpoints.

Group-IB offers a full range of solutions for data leak detection. Group-IB Digital Risk Protection monitors open and dark web sources to detect sensitive data belonging to your organization that has leaked into the public domain. Group-IB Threat Intelligence helps discover compromised credentials, breached databases, and Git leaks. Thanks to continuous monitoring of the corporate infrastructure, Attack Surface Management allows you to spot potential sources of data leaks, while Managed XDR detects and prevents data exfiltration. The Compromise Assessment service enables you to detect the unnoticed breaches.

Like any cybersecurity incident, data leakage requires a prompt and professional response. The Group-IB Incident Response Retainer is a pre-negotiated statement of work that enables an immediate action to be initiated, blocking the data leak to reduce the scope of damage and avoid penalties.

Common effects of data leakage are reputational losses leading to customer churn, terminated partner agreements, and eventually decreased profits
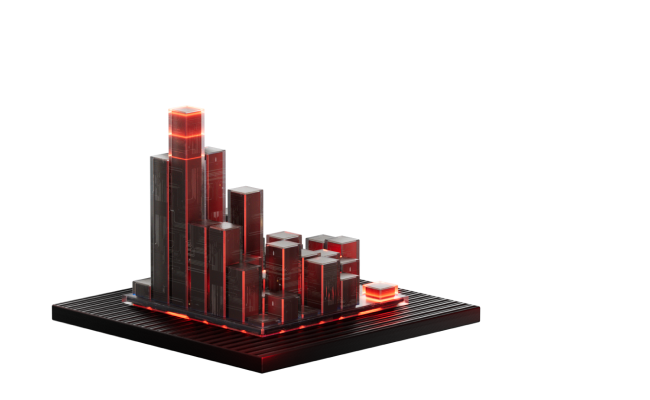
Average decline in the stock values after a data breach
Regularly assessing a business’s security posture is crucial to defend against data leaks caused by critical vulnerabilities. The first step is to uncover hidden breaches with Compromise Assessment. During the procedure, Group-IB experts may use the Managed XDR solution for threat detection and response

Businesses often have a complex and extensive IT infrastructure, making it challenging to keep track of all its components. Shadow IT assets such as forgotten web applications or remote computers can carry a high risk of data leakage.
An Attack Surface Management solution helps continuously discover unmanaged IT assets and identify vulnerabilities in your ecosystem. Meanwhile, the expert Security Assessment provides a comprehensive analysis of the company’s infrastructure, allowing to discover hidden vulnerabilities, weak spots, and security risks.

The Endpoint Detection and Response module of the Group-IB Managed XDR solution protects computers and servers against data leaks by detecting breaches and attacks on the host level. It uses intelligence data, signature and behavioral analysis, and malware detonation capabilities. Group-IB Fraud Protection solution completes the endpoint protection by protecting web and mobile API endpoints.

Group-IB offers a full range of solutions for data leak detection. Group-IB Digital Risk Protection monitors open and dark web sources to detect sensitive data belonging to your organization that has leaked into the public domain. Group-IB Threat Intelligence helps discover compromised credentials, breached databases, and Git leaks. Thanks to continuous monitoring of the corporate infrastructure, Attack Surface Management allows you to spot potential sources of data leaks, while Managed XDR detects and prevents data exfiltration. The Compromise Assessment service enables you to detect the unnoticed breaches.

Like any cybersecurity incident, data leakage requires a prompt and professional response. The Group-IB Incident Response Retainer is a pre-negotiated statement of work that enables an immediate action to be initiated, blocking the data leak to reduce the scope of damage and avoid penalties.

Regulatory bodies consider data leakage a violation of the data protection requirements, which often result in significant fines and legal cross-checks
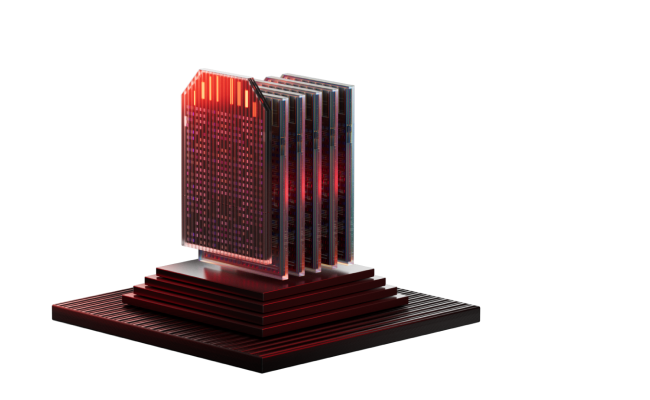
Amazon was issued a fine for breaches of the GDPR in 2021
Regularly assessing a business’s security posture is crucial to defend against data leaks caused by critical vulnerabilities. The first step is to uncover hidden breaches with Compromise Assessment. During the procedure, Group-IB experts may use the Managed XDR solution for threat detection and response

Businesses often have a complex and extensive IT infrastructure, making it challenging to keep track of all its components. Shadow IT assets such as forgotten web applications or remote computers can carry a high risk of data leakage.
An Attack Surface Management solution helps continuously discover unmanaged IT assets and identify vulnerabilities in your ecosystem. Meanwhile, the expert Security Assessment provides a comprehensive analysis of the company’s infrastructure, allowing to discover hidden vulnerabilities, weak spots, and security risks.

The Endpoint Detection and Response module of the Group-IB Managed XDR solution protects computers and servers against data leaks by detecting breaches and attacks on the host level. It uses intelligence data, signature and behavioral analysis, and malware detonation capabilities. Group-IB Fraud Protection solution completes the endpoint protection by protecting web and mobile API endpoints.

Group-IB offers a full range of solutions for data leak detection. Group-IB Digital Risk Protection monitors open and dark web sources to detect sensitive data belonging to your organization that has leaked into the public domain. Group-IB Threat Intelligence helps discover compromised credentials, breached databases, and Git leaks. Thanks to continuous monitoring of the corporate infrastructure, Attack Surface Management allows you to spot potential sources of data leaks, while Managed XDR detects and prevents data exfiltration. The Compromise Assessment service enables you to detect the unnoticed breaches.

Like any cybersecurity incident, data leakage requires a prompt and professional response. The Group-IB Incident Response Retainer is a pre-negotiated statement of work that enables an immediate action to be initiated, blocking the data leak to reduce the scope of damage and avoid penalties.

Both public and private companies can suffer severe damage to their brand value, experience a drop in shares, and lose the trust of vendors and customers due to data leaks
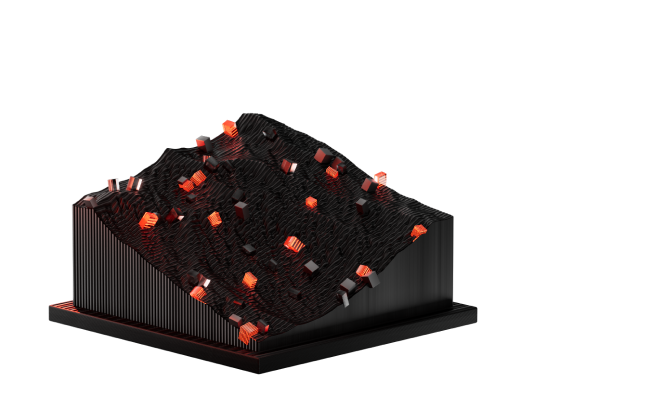
of data breach victims lost trust in the organization
Regularly assessing a business’s security posture is crucial to defend against data leaks caused by critical vulnerabilities. The first step is to uncover hidden breaches with Compromise Assessment. During the procedure, Group-IB experts may use the Managed XDR solution for threat detection and response

Businesses often have a complex and extensive IT infrastructure, making it challenging to keep track of all its components. Shadow IT assets such as forgotten web applications or remote computers can carry a high risk of data leakage.
An Attack Surface Management solution helps continuously discover unmanaged IT assets and identify vulnerabilities in your ecosystem. Meanwhile, the expert Security Assessment provides a comprehensive analysis of the company’s infrastructure, allowing to discover hidden vulnerabilities, weak spots, and security risks.

The Endpoint Detection and Response module of the Group-IB Managed XDR solution protects computers and servers against data leaks by detecting breaches and attacks on the host level. It uses intelligence data, signature and behavioral analysis, and malware detonation capabilities. Group-IB Fraud Protection solution completes the endpoint protection by protecting web and mobile API endpoints.

Group-IB offers a full range of solutions for data leak detection. Group-IB Digital Risk Protection monitors open and dark web sources to detect sensitive data belonging to your organization that has leaked into the public domain. Group-IB Threat Intelligence helps discover compromised credentials, breached databases, and Git leaks. Thanks to continuous monitoring of the corporate infrastructure, Attack Surface Management allows you to spot potential sources of data leaks, while Managed XDR detects and prevents data exfiltration. The Compromise Assessment service enables you to detect the unnoticed breaches.

Like any cybersecurity incident, data leakage requires a prompt and professional response. The Group-IB Incident Response Retainer is a pre-negotiated statement of work that enables an immediate action to be initiated, blocking the data leak to reduce the scope of damage and avoid penalties.

