
Get 24/7 incident response assistance from our global team
- APAC: +65 3159 4398
- EU & NA: +31 20 890 55 59
- MEA: +971 4 540 6400
Get 24/7 incident response assistance from our global team
Please review the following rules before submitting your application:
1. Our main objective is to foster a community of like-minded individuals dedicated to combatting cybercrime and who have never engaged in Blackhat activities.
2. All applications must include research or a research draft. You can find content criteria in the blog. Please provide a link to your research or research draft using the form below.







Group-IB Threat Intelligence provides unparalleled insight into your adversaries and maximizes the performance of every component of your security with strategic, operational and tactical intelligence
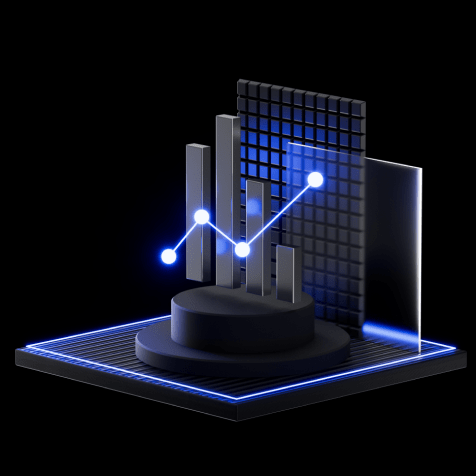
Understand threat trends and anticipate specific cyber attacks with thorough knowledge of your threat landscape. Group-IB Threat Intelligence provides precise, tailored and reliable information for data-driven strategic decisions.
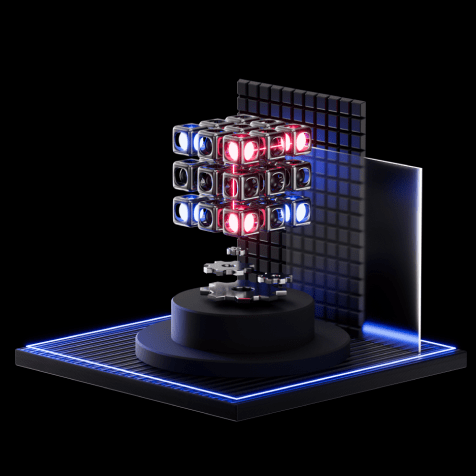
Strengthen defenses with detailed insight into attacker behaviors and infrastructure. Group-IB Threat Intelligence delivers the most comprehensive insight into past, present and future attacks targeting your organization, industry, partners, and clients.
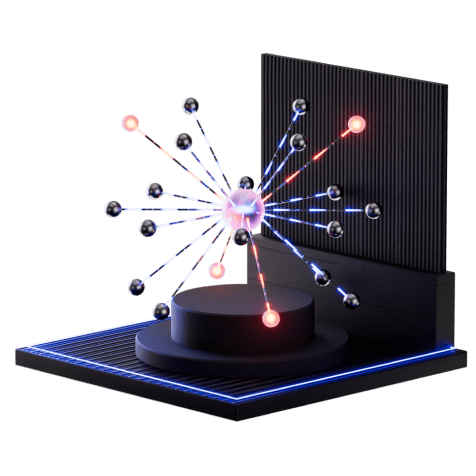
Identify cyber attacks faster and reduce response time with comprehensive visibility of the stages of attack used by threat actors. Group-IB Threat Intelligence gives your teams the best possible insight into the methods used by adversaries.

with tailored on-demand, and regular monthly and quarterly threat reports written by threat intelligence analysts specifically for the board and executives

with actionable threat intelligence before expanding into a new region/business line, and get industry-specific threats before digital transformation

of cyber security by avoiding unnecessary purchases and postponing upgrades by maximizing the efficacy of your existing security investments

and adapt instantly, use the insights to block malicious network and endpoint activity the moment it is first observed anywhere in the world

before they are exploited by arming your Red Team with detailed knowledge of threat actor’s tools, tactics and processes

and improve team efficiency by enriching your SIEM, SOAR, EDR and vulnerability management platforms with out-of-the-box API integrations supporting TAXII and STIX

for your technology stack with automated alerts that inform you the moment vulnerabilities are discovered or exploited by threat actors targeting your industry

and focus on legitimately risky events with a database of indicators of compromise for cybercriminals in your threat landscape

and quickly remove attackers from your network with knowledge of the cyber kill chain used by threat actors in the MITRE ATT&CK matrix format

Paste sites
Code repositories
Exploit repositories
Social media discussions
URL sharing services
C&C server analysis
Darkweb markets
Darkweb forums
Instant Messengers data (Telegram, Discord)
Phishing and malware kits
Compromised data-checkers
Detonation platform
Malware emulators
Malware configuration files extraction
Public sandboxes
ISP-level sensors
Honeypot network
IP scanners
Web crawlers
Malware reverse engineers
Undercover dark web agents
DFIR and audit services
Law enforcement operations
Regional specialists
Embedded managed service teams
CVE list
Exploit repositories
Dark web discussions
Threat campaigns mapping
This specialized offering enables you to submit requests to our seasoned threat intelligence researchers, skilled in analyzing and interpreting complex threat landscapes.
Threat Intelligence is a scope of data (or database) collected from various sources, processed and analyzed to provide a deep insight into adversary behavior, their motives, and attack tactics. Cyber Threat Intelligence empowers security teams to make faster and data-driven cybersecurity decisions and switch from reactive to proactive approach to fighting against threat actors.
Group-IB Threat Intelligence Services provide unparalleled insight into threat actors and optimizes the performance of every component of your security with strategic, operational, and tactical intelligence.
A threat intelligence platform (TIP), also known as a cyber threat intelligence platform, is a technology solution for gathering, combining, and organizing threat intelligence from various sources.
Threat intelligence platforms empower effective and precise threat identification, investigation, and response by providing a security team with information about threats in an easily-digestible format.
Solutions of this class automate data collection and management so threat intelligence analysts can focus on actually analyzing and researching cybersecurity threats. Additionally, threat intelligence platforms facilitate communicating threat intelligence information for security specialists.
To get started simply fill in the form on this page. Our threat intelligence team will guide you through the proof of concept process and show you how to get the most value out of your Threat Intelligence solution.
Threat Intelligence is a cloud service and can be enabled instantly. The Group-IB onboarding team will help configure the solution to meet your specific intelligence requirements and support integration with third-party services.
Group-IB Threat Intelligence is modular and flexible, allowing you to gather the intelligence you need how and when you need it. We believe that intelligence should be accessed and do not charge per user, integration or API call.
Group-IB Threat Intelligence utilizes Threat Hunting Rules, enabling intelligence to be filtered and refined to meet your exact needs. Our team will set these up when the solution is first enabled and will work with you to continuously refine them, your team can also add/remove/modify any rule to customize the intelligence to your exact needs.
With numerous successful deployments worldwide, we can provide case studies to help you build a business case for Threat Intelligence. Reach out to our friendly team to learn how we have improved security and provided return on investment in organizations for any sector.
Group-IB Threat Intelligence is powered by the Unified Risk Platform, the platform collects, correlates, and applies intelligence that is gathered from every function of Group-IB. This provides us with a uniquely diverse set of sources:
Malware intelligence
Data intelligence
Human intelligence
Sensor intelligence
Vulnerability intelligence
Open-source intelligence